ISO standards play a crucial role in helping businesses enhance their operations, gain a competitive edge, and ensure customer satisfaction. These standards provide a globally recognized framework for organizations to establish best practices and improve their efficiency and effectiveness.
With the need to comply with stringent data protection laws and ever-present concern of a data breach, organizations must adopt a robust framework to ensure the responsible governance of personal data. Enter the ISO/IEC 27559 standard for privacy enhancing data de-identification framework – a game-changer in the realm of data protection. The ISO/IEC 27559 standard builds upon the ISO/IEC 20889:2018 standard, which focuses on privacy-enhancing data de-identification terminology and techniques. This ISO/IEC 27559 provides organizations with an implementation framework for de-identification, offering guidelines and principles for effectively applying de-identification practices in accordance with the privacy principles in ISO/IEC 29100. In this article, we will explore how this framework revolutionizes data de-identification and empowers organizations to navigate the complex landscape of privacy regulations at speed and at scale.
Why data de-identification matters:
Data de-identification enables organizations to leverage sensitive data while preserving privacy. By transforming personal data in such a way that it no longer identifies individuals, organizations can unlock the value of data for various purposes like complying with data protection regulations, supporting the secondary use of data for research and analytics, and fostering trust among individuals whose data is being processed.
However, it is essential to understand the risks associated with re-identification. Re-identification refers to the process of linking de-identified data back to the individuals it represents. If not properly de-identified, data can still contain subtle patterns or unique attributes that, when combined with external information, could potentially identify individuals. This poses privacy risks and could lead to unauthorized disclosure or unintended consequences.
The publication of the ISO/IEC 27559 standard is highly significant as ISO, known for providing globally recognized frameworks, is likely to play a pivotal role in harmonizing de-identification practices across jurisdictions. This comprehensive ISO/IEC 27559 standard sets forth best practices, methodologies, and governance principles for the responsible and effective de-identification of data throughout its entire lifecycle.
Empowering compliance and credibility:
The ISO/IEC 27559 framework is far more than just another box to tick; it offers organizations invaluable support and guidance in how to meet their compliance obligations under privacy laws and regulations. While not mandatory, this international standard is gaining wide acceptance and recognition, making it a credible and applicable solution across jurisdictions. By adopting this framework, organizations can demonstrate their commitment to effective data de-identification practices on a global scale.
Navigating the ISO/IEC 27559 framework:
This ISO/IEC 27559 standard aims to address the identification and mitigation of re-identification risks, as well as risks associated with the lifecycle of de-identified data. It is applicable to organizations of all types and sizes such as public and private companies, government entities, and not-for-profit organizations. This standard covers controllers and processors who are engaged in data de-identification processes for the purpose of enhancing data privacy.
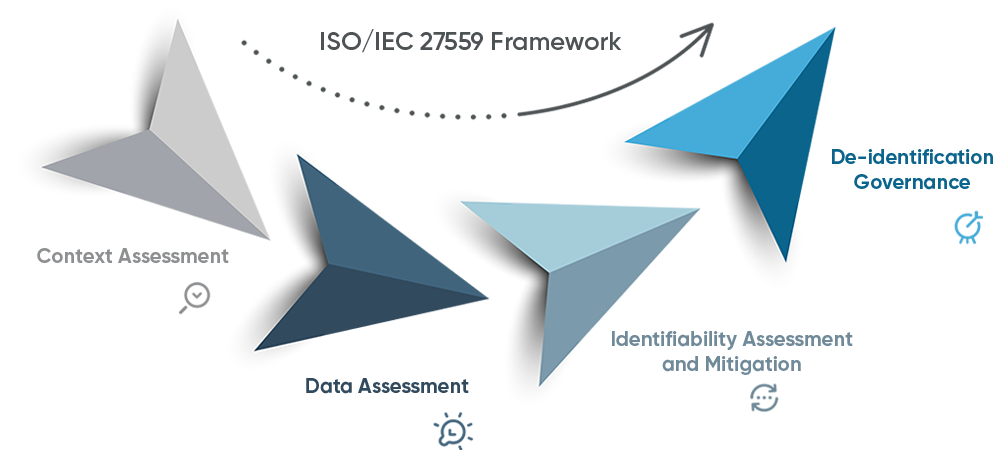
The ISO/IEC 27559 framework revolves around four key areas: context assessment, data assessment, identifiability assessment, and governance. Let’s dive into each of these areas to better understand their significance:
Context assessment: Privacy risks often stem from the context in which data is accessed, shared, or released. Evaluating this environment is crucial for scoping the de-identification process and identifying potential risks. Factors such as data source, intended use, transparency levels, and legal requirements must be considered.
Data assessment: Understanding data features and conducting an identifiability assessment are essential for safeguarding privacy while meeting use case requirements. This involves evaluating vulnerabilities, data types, attribute types, and data set properties. Through these assessments, unnecessary elements can be removed, reducing complexity and minimizing the need for extensive technical analysis.
Identifiability assessment and mitigation: Assessing and quantifying the identifiability of shared or released data is vital. Plausible disclosure scenarios, identifiability thresholds, and mitigation measures, such as data transformation and reconfiguring the data environment, help reduce risks. By adopting these measures, organizations can achieve a balance between privacy protection and data utility.
De-identification governance: To ensure ongoing risk mitigation, organizations must establish robust governance structures. This involves formalizing principles, policies, and procedures for data security, handling, management, storage, and sharing or release. Assigning roles and responsibilities, providing staff training, conducting privacy impact assessments, and implementing measures for incident response and ongoing monitoring are key components of effective de-identification governance.
Taking privacy protection to the next level:
The ISO/IEC 27559 framework equips organizations with the tools and guidance necessary to ensure their compliance with data protection laws and regulations. By adopting this framework, organizations strengthen their data de-identification practices and demonstrate their commitment to protecting individuals’ privacy globally.
We have highlighted the key areas covered within the ISO/IEC 27559 standard but how does an organization best operationalize the key principles of the standard.
At Trūata, we reviewed the four core areas and within each, we identified the key requirements to meet the standard. We then used this as a template to carry out an audit of our own internal processes.
When doing so we carefully considered each requirement, and assessed if our current business processes met the standard and if we could provide evidence to support this.
This approach provided us with a gap analysis to see if there was any delta between our organization’s current business processes and the requirements.
In our case, once we had gone through this process, we were easily able to measure our adherence to the standard and if there were any areas for improvement. While there is no formal certification for this standard as of yet we were able to accurately review, analyze and document our alignment to ISO/IEC 27559.
Accelerating compliance with Trūata Calibrate:
As organizations strive to meet the requirements of the ISO/IEC 27559 standard for privacy enhancing data de-identification framework, they need a reliable and efficient solution to assess, measure and address re-identification risks.
Trūata has developed a best in class, easy to use and deploy software solution specifically for this purpose. Trūata Calibrate offers a range of functionalities to support organizations in their journey towards ISO/IEC 27559 compliance specifically when it comes identifiability assessment, including identifying both direct and indirect risks and mitigation of such risks when it comes to personal data. Trūata Calibrate is a comprehensive solution that enables organizations to evaluate their data sets and quantitatively measure and mitigate the associated re-identification risks. By conducting this assessment, organizations have the tools available to them to ensure they can best meet the relevant standards and regulations.
Don’t miss the opportunity to revolutionize your data de-identification practices and join the forefront of privacy-enhancing solutions. Click the link to learn more about Trūata Calibrate and its functionalities in measuring and mitigating privacy risks.
For a more comprehensive understanding click to preview the ISO/IEC 27559 standard or purchase the standard.